Study Guide
Field 194: Computer Science
Recommendation for individuals using a screenreader: please set your punctuation settings to "most."
Sample Selected-Response Questions
The following reference material will be available to you during the test:
Competency 0001
Impacts of Computing
1. A property management company adopts an application screening system that uses machine learning to vet potential tenants. The system is trained only on public records and rental applications. After being trained on a large number of examples, the system uses data on an applicant to recommend whether or not the management company should accept their application. Which factor of this system is most likely to produce biased results?
- imbalances in input data that are then learned by the system
- failing to include additional data sources such as medical records
- selection of an industry standard machine learning architecture for the system
- usage errors by end users of the system at the management company
- Enter to expand or collapse answer. Answer expanded
- Correct Response: A. This item requires examinees to demonstrate understanding of ways computer systems are used in human decision-making, including how the design of the systems may promote inclusivity or introduce bias. Imbalances in input data that are then learned by the system can cause biased results in a machine-learning application screening system. Machine-learning systems heavily rely on the data they are trained on to make predictions or recommendations. Imbalanced input data can result in biased results. For example, if the training data predominantly includes rental applications from a specific demographic, the system might favor similar applications and unfairly disadvantage others. This can lead to biased results and discriminatory practices, undermining fairness and inclusivity in decision-making.
Competency 0001
Impacts of Computing
2. Which modification to a website would most effectively increase access for visitors with visual impairments who access the web with the help of screen reading software?
- designing the website to feature high-contrast backgrounds and large buttons and links
- making select information accessible using keyboard shortcuts and the TAB key
- including descriptive attributes for page elements within HTML tags
- creating a content flow for the screen reader that matches that of the web page
- Enter to expand or collapse answer. Answer expanded
- Correct Response: C. This item requires examinees to demonstrate knowledge of features of technology devices and software (e.g., alternative text for images, screen reader, text-to-speech, web accessibility tools) that improve accessibility and usability to address the diverse needs of all users and meet standard compliance requirements. Including descriptive attributes for page elements within HTML tags provides text descriptions of non-text content for screen readers. By including descriptive attributes within HTML tags, web developers ensure that all users, regardless of their abilities, can understand and navigate the website.
Competency 0001
Impacts of Computing
3. Which software development project would most likely be impacted by United States federal privacy laws?
- organizing the structure of and access to patient records at a hospital
- creating a social application for adults to share photos and video clips
- allowing website visitors to drop pins on a publicly viewable map
- storing customer and sales information for a company selling industrial equipment
- Enter to expand or collapse answer. Answer expanded
- Correct Response: A. This item requires examinees to demonstrate knowledge of rules, laws, and regulations related to the development and use of computing technologies and digital information (e.g., with respect to privacy, intellectual property rights, licensing, or hacking), including those that apply in educational settings (e.g., CIPA, COPPA, FERPA), and their impact on various stakeholders. This knowledge is expressed practically by knowing how and when software development and technology use are likely to be influenced by regulation. Organizing the structure of and access to patient records at a hospital would be most impacted by U.S. federal privacy laws. Patient records contain sensitive personal health information that is protected under U.S. federal privacy laws, such as the Health Insurance Portability and Accountability Act (HIPAA). Software projects must comply with these regulations to ensure the security and privacy of data.
Competency 0002
Computational Thinking and Programming
4. Use the flowchart excerpt to answer the question that follows.
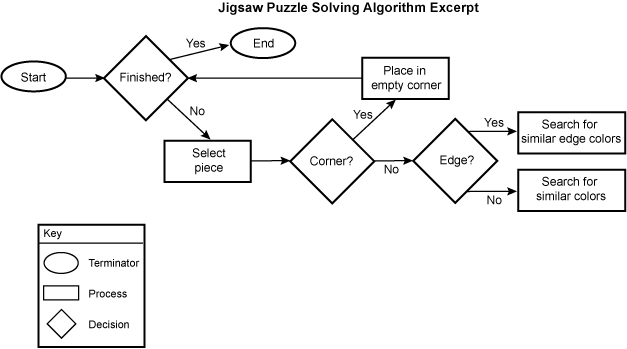
A flowchart is titled "Jigsaw Puzzle Solving Algorithm Excerpt." It begins with a "Start" terminator, leading to a decision diamond labeled "Finished?" with two possible outcomes: "Yes" and "No." If "Yes," the flowchart proceeds to an "End" terminator. If "No," it proceeds to a process box labeled "Select piece."
From "Select piece," the flowchart proceeds to another decision diamond labeled "Corner?" with two outcomes: "Yes" and "No." If "Yes," it proceeds to a process box labeled "Place in empty corner." From the process box, the flowchart proceeds back to the decision diamond labeled "Finished?"
If "No" is selected for "Corner?" the flowchart proceeds to another decision diamond labeled "Edge?" with two outcomes: "Yes" and "No."
If the answer to "Edge?" is "Yes," the flowchart proceeds to a process box labeled "Search for similar edge colors." If "No," it proceeds to a process box labeled "Search for similar colors."
At the bottom of the flowchart, there is a key explaining the symbols used: a circle for "Terminator," a diamond for "Decision," and a rectangle for "Process."
Which jigsaw-solving algorithm excerpt description accurately represents the portion of the flowchart shown?
-
- If the puzzle is not finished, select each puzzle piece.
- Compare each corner to the picture on the puzzle box before placing.
- Compare each edge to the picture on the puzzle box before placing.
- Compare each normal piece to the picture on the puzzle box before placing.
-
- If the puzzle is not finished, select a puzzle piece.
- If the piece is a corner, place it in a corner of the workspace.
- If the piece is an edge, use color-matching to help build the frame of the puzzle.
- If there is no piece in the center of the table, place any normal piece in the center.
-
- If there are no unselected pieces, go to x.
- Select a puzzle piece.
- If the piece is a corner, set it aside until the end. Return to 1.
- If the piece is an edge, set it aside until the end, separate from the corners. Return to 1.
-
- If the puzzle is not finished, select a puzzle piece.
- If the piece is a corner, place it in an empty corner. Return to 1.
- If the piece is an edge, search for similar edge colors.
- If similar edge colors are found, rotate and attempt to place it in the puzzle.
- Enter to expand or collapse answer. Answer expanded
- Correct Response: D. This item requires examinees to apply knowledge of formats for representing algorithms (e.g., flowcharts, pseudocode, block-based visuals) to translate between informationally equivalent representations of an algorithm. The flowchart represents an iterative process for solving a jigsaw puzzle by starting with corners and edges, and then matching colors. This description aligns with an approach to solving puzzles and the logical steps depicted in the flowchart. The algorithm begins by selecting a puzzle piece and placing it based on its type (corner or edge) and color matching. The other descriptions describe other algorithms for jigsaw puzzle solving.
Competency 0002
Computational Thinking and Programming
5. Use the code snippet to answer the question that follows.
01 forward-slash asterisk Turtle is a class that traces lines onscreen and includes
02 the methods .forward(float length) and .left(float angle) asterisk forward-slash
03
04 Turtle t = Turtle()
Each code snippet draws an identical square. Which code snippet can be modified to draw a different polygon by updating only a single line of code?
-
01 function shape1()
02 float length = 100
03 t.forward(length)
04 t.left(90)
05 t.forward(length)
06 t.left(90)
07 t.forward(length)
08 t.left(90)
09 t.forward(length)
10 t.left(90)
11
12 shape1()
-
01 function shape2()
02 float length = 100
03 for(int i = 0; i is less than 4; i = i +1)
04 t.forward(length)
05 t.left(90)
06
07 shape2()
-
01 function shape3(float length)
02 for(int i = 0; i is less than 4; i = i + 1)
03 t.forward(length)
04 t.left(90)
05
06 shape3(100)
-
01 function shape4(float sides, float length)
02 if(sides is greater than 2)
03 float degrees = 360 divided by sides
04 for(int i = 0; i is less than sides; i = i + 1)
05 t.forward(length)
06 t.left(degrees)
07
08 shape4(4, 100)
09
- Enter to expand or collapse answer. Answer expanded
- Correct Response: D. This item requires examinees to apply knowledge of expressions and operators (e.g., arithmetical, relational, logical). The function shape4 can be modified to draw a different polygon by updating only a single line of code. This function allows for the creation of various polygons by changing the number of sides. The function calculates the angle to turn based on the number of sides and uses a loop to draw each side of the polygon. By modifying the line that specifies the number of sides, the drawn shape can be flexibly altered.
Competency 0002
Computational Thinking and Programming
6. Use the code snippet to answer the question that follows.
01 forward-slash asterisk The two-dimensional array network models the relationships
02 among four people. The four people are each represented by a
03 column and again by a row. If two people know one another,
04 the intersection of their row and column is TRUE. asterisk forward-slash
05
06 bool[][] network = [[FALSE, TRUE, FALSE, FALSE],
07 [TRUE, FALSE, TRUE, TRUE],
08 [FALSE, TRUE, FALSE, FALSE],
09 [FALSE, TRUE, FALSE, FALSE]]
10
11 forward-slash asterisk count the number of relationships asterisk forward-slash
12
13 function traverse(bool[][] mat)
14 int n = mat.size[0]
15 int count = 0
16
17 for (int j = 0; j is less than n; j = j + 1)
18 for (int k = 0; k is less than n; k = k + 1)
19 if(mat[j, k] == TRUE)
20 count = count + 1
21 return count divided by 2
22
23 int edges = traverse(network)
Which replacement for lines 17–21 of the code snippet best refactors the traverse() function in a way that preserves the function's accuracy using this example while improving its efficiency?
-
17 for (int j = 0; j is less than n; j = j + 1)
18 for (int k = 1; k is less than n; k = k + 1)
19 if(mat[j, k] == TRUE)
20 count = count + 1
21 return count
-
17 for (int j = 1; j is less than n; j = j + 1)
18 for (int k = 0; k is less than n; k = k + 1)
19 if(mat[j, k] == TRUE)
20 count = count + 1
21 return count
-
17 for (int j = 0; j is less than n; j = j + 1)
18 for (int k = j + 1; k is less than n; k = k + 1)
19 if(mat[j, k] == TRUE)
20 count = count + 1
21 return count
-
17 for (int j = 1; j is less than n; j = j + 1)
18 for (int k = j - 1; k is less than n; k = k + 1)
19 if(mat[j, k] == TRUE)
20 count = count + 1
21 return count
- Enter to expand or collapse answer. Answer expanded
- Correct Response: C. This item requires examinees to analyze algorithms to predict outcomes, compare advantages and disadvantages of two or more differing implementations, and determine trade-offs. Option C best refactors the traverse() function while improving its efficiency. This refactoring halves the number of comparisons by avoiding redundant checks. In the original code, each pair of relationships is checked twice (once for [i, j] and once for [j, i]). By starting the inner loop at j + 1, the refactored code ensures each pair is only checked once.
Competency 0003
Networks, the Internet, and System Design
7. Which physical location within a computer is most appropriate for the storage of a value that must be accessed quickly and used for immediate computation?
- cache
- random access memory
- register
- disk drive
- Enter to expand or collapse answer. Answer expanded
- Correct Response: C. This item requires examinees to demonstrate knowledge of basic elements of computing devices and their functions (e.g., input, output, processing, storage), as well as interactions between application software, operating systems, and hardware. A register is the most appropriate storage location for fast access and immediate computation. Registers are small, fast storage locations within the CPU, directly connected to the arithmetic and logic unit ( A L U ) that hold data to be processed immediately. In contrast, cache, RAM, and disk drives have slower access times due to their distance from the CPU.
Competency 0003
Networks, the Internet, and System Design
8. Internet Protocol ( I P ) packets include a checksum field as part of the header. The purpose of this checksum field is to:
- detect data corruption or manipulation.
- direct the packet to the correct destination.
- test the computer’s arithmetic and logic unit.
- ensure data is decoded in the order it was transmitted.
- Enter to expand or collapse answer. Answer expanded
- Correct Response: A. This item requires examinees to demonstrate knowledge of the protocols for connecting devices and transmitting data over the Internet. An I P packet header's checksum field is meant to detect data corruption or manipulation. The checksum is a value calculated from the packet's contents that allows the receiving device to detect errors. Nonmatching checksum values act as a check on data reliability and can prompt data retransmission.
Competency 0003
Networks, the Internet, and System Design
9. A factory produces wireless speakers and assigns media access control (MAC) addresses during production. The most significant 24 bits of the address identify the manufacturer, while the least significant 24 bits increment up from a random value chosen at the beginning of each day. The first speaker produced on a given day was assigned the hexadecimal address 66, B 4, F B, 42, A 9, 94 . Five hundred fifty-three speakers were produced before the assembly line was shut down for a meal break. Which MAC address will be assigned to the first speaker produced after the meal break?
- 66, B 4, F B, 42, A B, B E
- 66, B 4, F B, 42, A E, F 8
- 66, B 7, 25, 42, A 9, 94
- 66, C 4, F B, 52, B 9, A 4
- Enter to expand or collapse answer. Answer expanded
- Correct Response: A. This item requires examinees to demonstrate knowledge of number systems (e.g., binary, hexadecimal) and their application in computing systems. The MAC address 66, B 4, F B, 42, A B, B E will be assigned to the first speaker produced after the meal break. The initial address is 66, B 4, F B, 42, A 9, 94 , and the least significant 24 bits ( 42, A 9, 94 ) need to be incremented by 553. Converting 553 to hexadecimal gives 2 2 9 , so adding this to the initial value results in the new address 66, B 4, F B, 42, A B, B E . This calculation ensures that the address increments correctly within the specified range.
Competency 0004
Cybersecurity
10. Use the code snippet to answer the question that follows.
01 char[] password characters =
02 ["A","B","C","D","E","F","G","H","I","J","K","L","M
03 ","N","O","P","Q","R","S","T","U","V","W","X","Y","
04 Z","a","b","c","d","e","f","g","h","i","j","k","l",
05 "m","n","o","p","q","r","s","t","u","v","w","x","y"
06 ,"z","0","1","2","3","4","5","6","7","8","9"]
An attacker attempts to brute force passwords by iterating through the password_characters array and constructing progressively longer String objects. Which password would be resilient against this attack for the greatest number of guesses?
- P A 5 5 W 0 R D
- 123abcABC123
- j39Mksji89
- redpickleholidaydance
- Enter to expand or collapse answer. Answer expanded
- Correct Response: D. This item requires examinees to apply knowledge of physical, digital, and behavioral safeguards for protecting and maintaining data integrity and availability. The password "redpickleholidaydance" would be resilient against a brute force attack for the greatest number of guesses. Longer passwords are more resistant to brute force attacks. "redpickleholidaydance" is the longest password, making it the most resilient against such attacks. Brute force attacks involve systematically guessing passwords, and longer passwords increase the number of possible combinations and make them harder and more time-consuming to guess.
Competency 0004
Cybersecurity
11. The Data Encryption Standard ( D E S ) is a symmetric encryption standard using a 56-bit key that was introduced in 19 77 . The United States National Institute of Standards and Technology ( N I S T ) no longer recommends D E S or similar standards, even in cases where weaknesses have not been published, for which primary reason?
- The age of the standards means vulnerabilities could have been discovered but not made public.
- The key sizes of the standards make them vulnerable to brute force attacks.
- Modern asymmetric encryption standards have replaced symmetric encryption standards.
- Every possible key for the standards has already been used.
- Enter to expand or collapse answer. Answer expanded
- Correct Response: B. This item requires examinees to demonstrate knowledge of purposes, applications, and limitations of cryptographic methods in data security. A 56-bit key is no longer considered secure against modern brute force attacks. Advances in computing power have made it feasible to try all possible key combinations within a reasonable time frame, rendering D E S vulnerable. Modern encryption standards use 128-bit or larger key sizes.
Competency 0004
Cybersecurity
12. Use the email excerpt to answer the question that follows.
Dear Valued Customer,
Hello, this message is from your bank. We need to verify your personal information, including social security number. Please click the link below and enter your information to verify. Feel free to call the number at the bottom of this message if you have any questions or concerns.
Click here to verify information
Sincerely,
Fraud Prevention Department
5 5 5, 3 3 3, 2 2 2 2
A user receives an email containing the text shown and is concerned about a security breach. Which step sufficiently safeguards the user’s private information?
- click the link and use the suggested website to request more information
- call the included bank phone number to verify the message
- contact the bank through their official website to investigate further
- close the associated bank account and cancel any linked debit cards
- Enter to expand or collapse answer. Answer expanded
- Correct Response: C. This item requires examinees to apply knowledge of actions to prevent or respond to digital security breaches. Contacting the bank through its official website best safeguards a user’s private information. Phishing emails often include links to fraudulent websites designed to steal personal information. By using the bank's official contact channels, a user can ensure they are communicating with the actual bank. This safeguards the user's private information and prevents unauthorized access to their accounts.
